2024 CrowdStrike Configuration Update Outage
2024-07-19What Happened
On July 19, 2024, cybersecurity firm CrowdStrike pushed a faulty configuration update to its Falcon sensor software for Windows systems. The update caused Windows machines to enter bootloops or crash with "blue screens of death," disrupting more than eight million computers worldwide and affecting airlines, banks, hospitals, broadcasters, and government agencies before a fix was deployed.
Outcome
Flights were grounded, services interrupted, and CrowdStrike’s stock price fell sharply. The company worked with customers to manually remediate affected systems, a process that took days for some organizations.
CrowdStrike faced lawsuits (including from Delta Air Lines) and regulatory scrutiny but retained much of its customer base. The incident became a case study in how a single misconfigured security update at a dominant provider can have global consequences.
Why It's Relevant Today
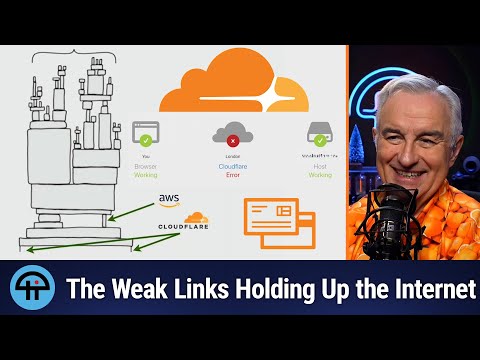
Like the 2025 Cloudflare outages, the CrowdStrike incident shows how flawed updates from centralized security infrastructure can ripple across critical services worldwide. Both cases highlight the need for stricter testing, staged deployment, and architectural safeguards around high-privilege security components.